History
Let’s begin with the history of bitcoin by outlining some of the relevant historical steps that led to its spread, from its birth and use related to only a few nerds and crypto geeks, to bitcoin’s global use as the world’s first cryptocurrency by capitalization:
- 2008: Bitcoin got its first public mention on October 31, 2008 on the Crypto Mailing List. In an e-mail, Satoshi Nakamoto, a pseudonym whose real identity is unknown (no one knows whether it is a single person or a group of people), published Bitcoin’s white paper and defined the idea of a peer-to-peer virtual currency independent of intermediaries such as central banking entities or trusted parties.
- 2009: The first version of Bitcoin software is released (version 0.1.0). This version, despite being in alpha format and entirely experimental, incorporates everything Nakamoto described and promised in the white paper release. Also in 2009, the first block, the so-called “genesis block,” is created and the bitcoin cryptocurrency begins to be traded.
- 2010: The first real transaction using bitcoin is made when a programmer (Laszlo Hanyecz) paid 10,000 bitcoins for two pizzas, worth about $41. This turns out to be a significant event as it represents the first payment in bitcoin for a good or service. Since then, the date of May 22, 2010 has been commemorated every year as Bitcoin Pizza Day.
- 2012: The first bitcoin exchanges are founded. “Bitcoin Central,” the first bitcoin exchange to operate under European regulation, is established.
- 2014: Several alternative platforms based on bitcoin fundamentals are introduced to the market.
- 2016: Blockchain becomes a trend. News outlets describe bitcoin as one of the most disruptive technologies in the digital world for years to come.
- 2018: Media-generated hype leads to the bursting of the bitcoin bubble and consequently the steady decline in the price of bitcoin throughout the year.
- 2021: El Salvador becomes the first country to accept bitcoin as legal tender. Bitcoin is now known globally.
How it works
Bitcoin, more than 10 years after its creation, remains the first cryptocurrency and the first blockchain in importance
Indeed, it boasts a network that is unparalleled in distribution and decentralization, in the cryptocurrency field, thus ensuring a very high level of security.
Although the real identity of Satoshi Nakamoto is not yet known, one can easily trace Bitcoin’s ideological roots to the cypherpunk movement, a group of libertarian activists who promoted the use of computer cryptography as a tool to lead to social and political, as well as economic, change. (https://nakamotoinstitute.org/static/docs/cypherpunk-manifesto.txt)
Indeed, when approaching Bitcoin, and thus the first realized blockchain, one must keep in mind that the stakes are much greater than one might think.
It is not a matter of pure speculation, as may be the case with many cryptocurrencies born later, but of a new cultural paradigm that challenges the existing one based on centralization and top-down dynamics, proposing as an alternative decentralization and its bottom-up dynamics.
Although this aspect is often left in the background, partly because Nakamoto never wasted too much time on political discourse, there are in fact statements of his that make explicit the importance of this aspect:
“Yes, [we will not find a solution to political problems in cryptography], but we can win a major battle in the arms race and gain a new territory of freedom for several years.
Governments are good at cutting off the heads of centrally controlled networks like Napster, but pure P2P networks like Gnutella and Tor seem to be holding their own.”
Also, it should not be forgotten that in the first blockchain block of Bitcoin, there is a note from Nakamoto, containing the title of an article in The Times newspaper:
“The Times 03/Jan/2009 Chancellor on brink of second bailout for banks.”
A clear reference to the instability of the banking system.

Based on these assumptions, Satoshi Nakamoto sought to create a system that could combat the centralization of finance as well as the inflation of FIAT currencies (the legal tender currencies), not coincidentally Bitcoin was born in the aftermath of the 2008 crisis.
To combat inflation, Nakamoto sought to replicate a natural mechanism, that of scarcity, as we will see in the next chapter, by applying it to a cryptocurrency, the ownership of which is transferred among various users through transactions that are recorded in a public ledger visible to all (the blockchain precisely).
Before we begin to explore the world of Bitcoin, however, two clarifications need to be made.
First, the concepts presented in this overview are always discussed at a high level to allow for greater understanding by all. There will be dedicated lectures to explore individual topics in more depth.
Second, when discussing Bitcoin, a distinction must be made between the protocol and the cryptocurrency.
For convenience we will always use the capital “b” (Bitcoin) when referring to the protocol, while the lowercase “b” (bitcoin) will be used to refer to the cryptocurrency, along with the abbreviation “BTC.”
Supply and scarcity
As mentioned, bitcoin is designed to create a digital scarcity that replicates that of physical commodities.
For this reason, a maximum limit of existing bitcoins(max supply) of 21 million (20,999,999,999.9769 to be precise) has been imposed at the code level.
These 21 million bitcoins were not put into circulation immediately but are distributed through a process called mining, which we will discuss in the chapter devoted to this topic.
In summary, each time a new block is added to the chain, an amount of bitcoin is mined, that is, new bitcoins are produced out of thin air.
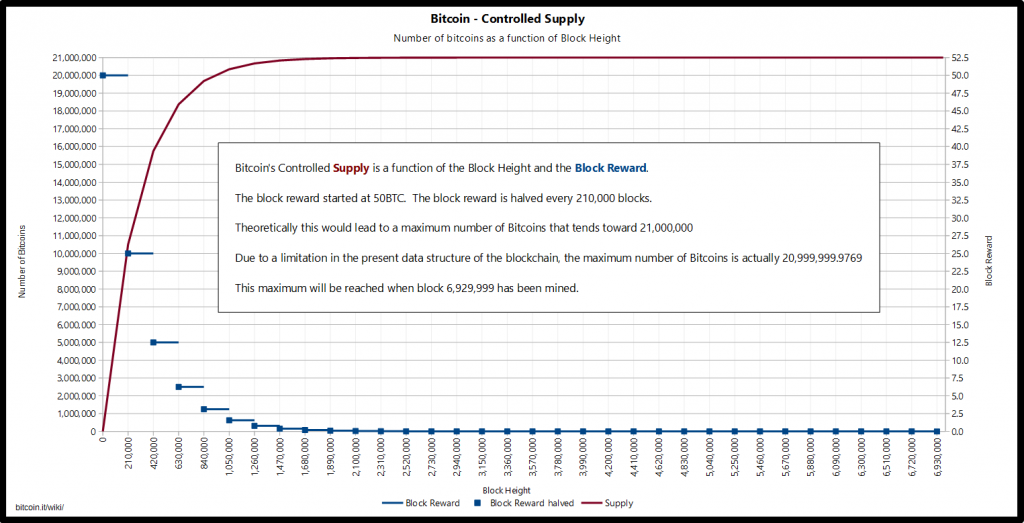
Initially, it was 50 bitcoins per block. However, this figure is gradually being reduced through a process called halving, which every 21000 blocks (about 4 years) halves the amount of bitcoins mined at each block.
About 19 million of the total 21 are currently in circulation. This means that about 2 million remain to be mined. As a result, due to halving and the fact that a new block is produced every 10 minutes or so, it is expected that all bitcoins will not be in circulation until 2140.
Halving is the basis of bitcoin’s economic model because it ensures a continuous decrease in the distribution of bitcoins, with the aim of fighting inflation with a deflationary trend.
In fact, a decrease in the rate of bitcoin distribution through mining tends to be matched by a gradual growth in the value of bitcoin, given precisely by scarcity.

In 2140, when all bitcoins are in circulation, it will no longer be possible to create any more bitcoins unless there are future changes to bitcoin’s protocol, which, however, in addition to being extremely complex, would have a particularly negative impact on bitcoin’s economy, as the effect of scarcity would be lost.
Network
A first issue of fundamental importance is that of Bitcoin’s network.
Bitcoin’s is a peer-to-peer (P2P) network built on the Internet.
Since it is a P2P network, all computers participating in the network (the nodes), are equal to each other, playing both the role of service providers and consumers.
It is a decentralized and open(permissionless) architecture, in that no one has to be asked for permission to join.
As a decentralized network, there are no central actors but only peer nodes, as envisioned by the P2P paradigm.
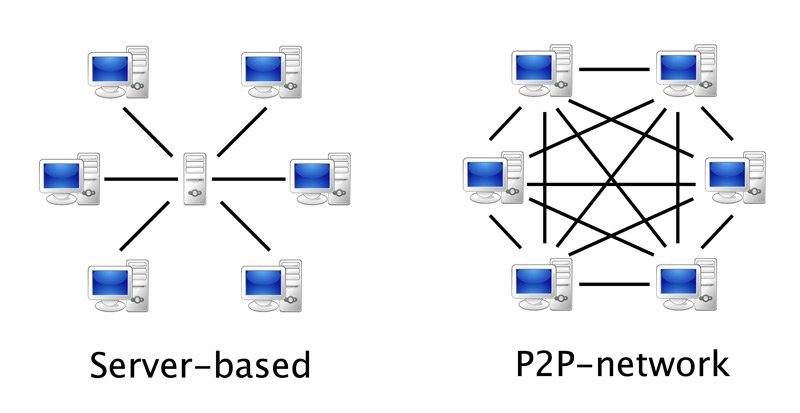
It can be argued that the Bitcoin network is the most successful real-world application of the P2P paradigm, along with file sharing, and it should be emphasized that, that of P2P, is not simply an architectural choice, but is a reflection of a definite social, political and cultural intent, which is what underlies Bitcoin and stems from the battles fought by the cypherpunk movement, as seen in the introduction.
Returning to the Bitcoin network, one must first distinguish between:
- Bitcoin network: the network of nodes using Bitcoin’s P2P protocol;
- ExtendedBitcoin network: the extended network that includes both users of Bitcoin’s P2P protocol and other additional protocols, such as pool-mining protocols, Stratum and so on.
Despite being a P2P network, nodes can have different roles and differ from each other according to the types of services they perform.
There are essentially 4 functions:
- Routing;
- Blockchain database;
- Mining;
- Wallet.
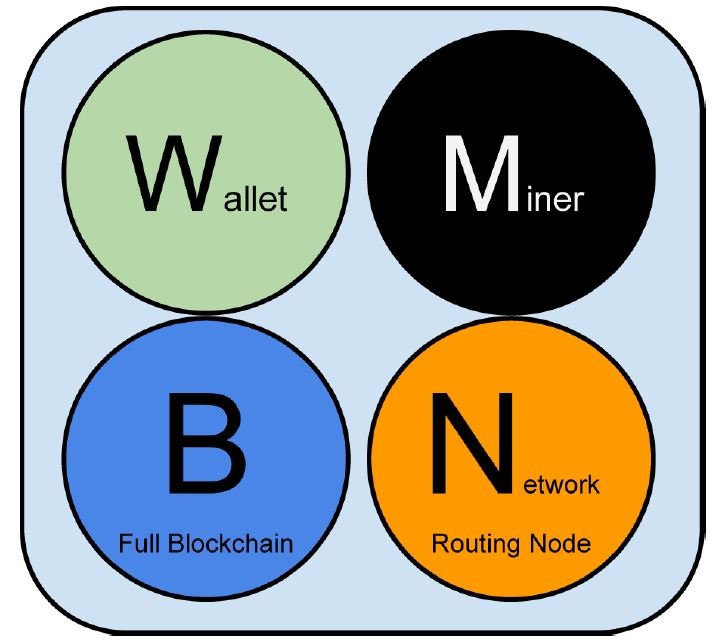
The routing function is common to all nodes and is necessary to participate in the network. Routing refers to the ability to validate and propagate transactions and blocks through the network, as well as being able to communicate with other nodes.
The other functions are optional.
The blockchain database function is to possess locally a full copy of the Bitcoin ledger, which is constantly synchronized and updated with other nodes in the network.
As can be imagined, the ledger takes up a lot of space (currently about 360 GB). Although it is much lighter than that of other blockchains, it still involves dedicated space availability.
Mining refers to the competition to create new blocks to add to the blockchain. This is a computationally onerous process that requires specific hardware. We will explain mining in more detail in the chapter on Proof of Work, Bitcoin’s consensus algorithm.
Finally, the wallet function is to manage users’ wallets, the wallets through which they manage their bitcoins.
Thus, there are several node types; we list the main ones here:
| Node type | Routing | Blockchain db | Miner | Wallet |
|---|---|---|---|---|
| Reference Client | ||||
| Full Blockchain Node | ||||
| Mining Node | ||||
| Lightweight Client (SVP) |
- Reference Client: this is the most popular client, Bitcoin Core, also called Satoshi client. This node type can perform all 4 functions;
- Full Blockchain Node: this is a node that has a copy of the Bitcoin ledger locally, constantly updated and synchronized with the rest of the network. Such a node can verify any transaction independently, without the need to refer to other nodes.
Bitcoin’s security is largely based on Full Blockchain Nodes, because they provide registry redundancy, as if there were thousands of backup copies, distributed around the world. - Mining Node: is a node that performs the function of mining, it does not necessarily have to also be a Full Blockchain Node, so it does not necessarily have to have a local copy of the ledger.
In particular, there is a distinction between solo miners, i.e., those who mine on their own and thus require a node containing a copy of the blockchain, and pool miners, nodes that do not have a local copy of the blockchain but combine their computational powers by creating precisely a mining pool, in which only the administrator will need to possess a local copy of the blockchain.
As specified earlier, a mining node requires dedicated hardware to solve the complicated cryptographic puzzles required to create the new blocks. - Lightweight client or SVP (Simplified Payment Verification): this is a node that performs only the wallet function (in addition to the routing function that, as mentioned above, is common to all types of nodes). Since this type of node does not possess a local copy of the blockchain, it has no particular need for space, nor for dedicated hardware, and merely performs the wallet function and communicates with other nodes, from which it obtains the information it needs.
These features make it suitable for installation in low-power devices, such as mobile devices.
The most prominent example of SVP are the various mobile wallets.
Having made the distinctions between nodes, it is worth reiterating the fact that the Bitcoin network is permissionless, that is, you do not have to ask anyone for permission to be part of it.
Anyone can download a Bitcoin client and become a node in the network.
Of the various clients, the most popular is the aforementioned Bitcoin Core, but there are others as well, in various languages.
Once one joins the network, our node will contact other nodes through a Bitcoin protocol called gossip protocol, which is the method used by nodes in the network to exchange messages.
Through message exchanges, communicating nodes will inform each other of their status, keeping each other up to date.
To learn more about the bitcoin network, we refer you to the dedicated lectures.
Account
Very often, especially if you are not computer literate, there is confusion between bitcoin network nodes and accounts.
We have already talked about nodes; let us now come to accounts and start by saying that the term “account” is incorrect. It is more correct to talk about ownership of bitcoin and therefore those who hold ownership of bitcoin.
In simpler terms, the question is, how does one become an owner of bitcoin?
To answer this, we are helped by cryptography, which is indispensable when dealing with blockchain and cryptocurrency.
Let’s start by dispelling a myth, that of anonymity in bitcoin. When you own bitcoins, this is not done anonymously, but through a pseudonym.
In short, a way is needed to identify a bitcoin possessor, thus being able to be certain that it is he who is carrying out transactions involving his possessions, but without in any way going to his privacy.
As we said, cryptography comes to our aid, and bitcoin possession is established through digital key pairs.
Each key pair consists of:
- Private key;
- Public key.
The latter can be thought of as a bank account number, while the former can be thought of as the PIN that grants control over the account.
It should be specified that these keys are not saved in any way in the Bitcoin network, but rather are saved by individual users in a file called a wallet, which is not to be shared on the network in any way.
In fact, the key pair is generated offline and it would be wise to keep it away from devices that have access to the network at all times.
The only thing that determines the possession of bitcoins is this key pair, and the only way to be able to spend them is the knowledge of the private key. Whoever has possession of our private key therefore, is able to spend our bitcoins.
In addition to the public key and the private key, there is a third element, the bitcoin address, which can be seen as the payee in a check.
The private key, the public key and the bitcoin address, are cryptographically bound together and are inseparable from each other.
In particular, they are derived through the use of mathematical functions that are practically irreversible, which is why they are referred to as asymmetric cryptography, because they are functions that can only be computed in one direction and not the other.
Specifically, the basis of Bitcoin cryptography is elliptic curve multiplication, which will not be explored in depth here but in dedicated lectures.
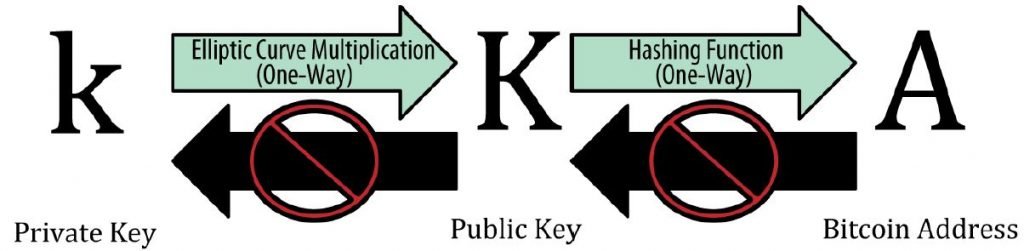
The important thing to understand is the link between private key, public key and bitcoin address, which we list not surprisingly in that order.
First, in fact, a private key is generated, which is nothing but a number between 1 and2256.
Starting from this number, by elliptic curve multiplication, the public key is obtained.
Finally, from the public key, the bitcoin address is obtained, via a hash function, which is a function that, given an input of arbitrary length, returns an output of fixed length.
Without going into the details of how hash functions and elliptic curve multiplication work, suffice it to understand that these are functions in which it is easy to do the calculations in one direction but virtually impossible to do them in the opposite direction.
Going from an input to an output (Hash sum) takes little time and effort; tracing the input back from the output is virtually impossible.
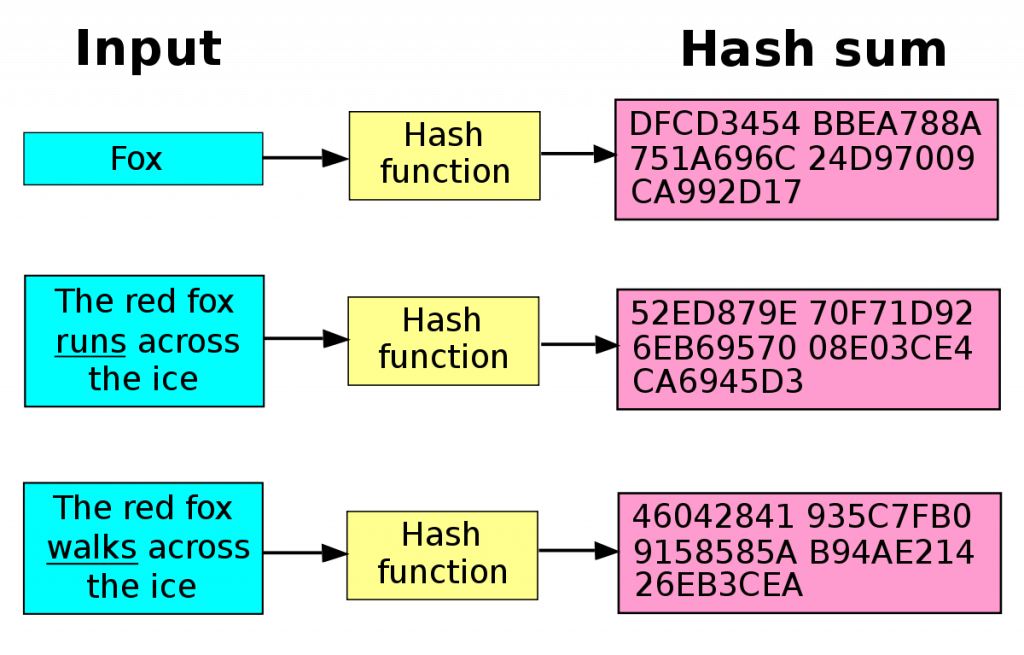
So it is essentially impossible, starting from a Bitcoin address, to trace back to the corresponding public key, but by owning the public key, it is easy to determine which Bitcoin address it is bound to.
Another fundamental concept is that of digital signature, i.e., a signature, produced through the private key, that makes it possible to establish the ownership of a transaction, who performed it. We will see more about digital signatures at work in the next chapter on transactions.
Let us now summarize the concepts exposed so far, defining schematically the usefulness of the various components:
- Private key: This is what allows bitcoins to be spent, through the creation of digital signatures. It must always remain secret, because those who know it are able to spend the bitcoins held;
- Public key: is generated by the private key and is what allows us to verify the validity of digital signatures, so it must be known by other actors to verify that the digital signatures we generate are correct and valid;
- Bitcoin address: this is the only piece of data that we will frequently see from normal users who transact with a wallet, it is public and known to everyone, and it is generated from the public key.
Once again, it should be emphasized that since this is an overview, we have simplified many concepts, which will be further discussed in the lessons devoted to individual topics.
Transactions
Simplifying things, we could say that the Bitcoin blockchain is nothing more than a register of transactions.
We have seen how the Bitcoin network is constituted, how possession of bitcoin is determined, let us now see how possession can be transferred.
Transactions are structured data that encode the transfer of value between bitcoin owners.
Let us take the simplest case, one in which there are two actors, one of whom wants to transfer bitcoins to another.
Let us take the case where Alice wants to send 1 bitcoin to Bob.
First, when approaching bitcoin, a conceptual error, based on a wrong metaphor, should be avoided.
It can happen to imagine bitcoins as the money we have in a bank account and which we can use through a credit card or an ATM.
This is a deeply flawed metaphor, which can lead to the construction of a completely wrong mental image of bitcoin.
It is much more correct to think of bitcoins as digital cash; in fact, typical cash mechanisms are reproduced in Bitcoin.
Let’s take an example: we are at the supermarket, arrived at the cash register we have to pay a total of 15 euros.
In the case of cash, let’s imagine that we have 1,000 euros in the account, what happens is that the 15 euros are deducted from the 1,000.
In the case of cash, since there is no 15 euro bill, we have to reach the amount to be paid with different denominations. We can use a 10-euro bill and a 5-euro bill, or we can use a 20-euro bill.
In the first case, the sum of the two bills gives the required total, but in the second case the bill is worth more than the required total.
Clearly, we cannot cut a 20-note into 4 parts, because it would no longer be valuable. We must therefore give the 20 bill and we will receive a 5 bill as change.
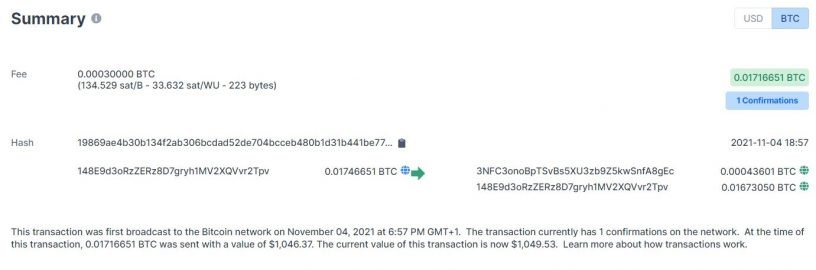
Bitcoin tries to replicate this mechanism, without having physical coins, of course, but inputs and outputs.
{
"ver": 1,
"locktime": 0,
"inputs": [
{
"sequence": 4294967295,
}, "witness": "",
"script": "4730440220786148b485f0d2f77cecdedb322301736c00d9d81e8c1d751fc3547aa7236ef0022038b8cd70833bd8982e9ecc8a11cbc04b6623bb0dffbe3563086d919f4d466f1701210352ae79b8d97a20356d3affbd440865f3dfddac92b13b106c67581f0a0e9235a4",
}, "index": 0,
"prev_out": {
"spent": true,
"script": "76a914224643d8742fa4c2545e69fa54a945dff1ff084688ac",
"spending_outpoints": [
{
"tx_index": 6788412058082531,
"n": 0
}
],
"tx_index": 4480999194101804,
}, "value": 1746651,
"addr": "148E9d3oRzZERz8D7gryh1MV2XQVvr2Tpv",
"n": 0,
}, "type": 0
}
}
],
"out": [
{
"type": 0,
"spent": false,
"value": 43601,
"spending_outpoints": [],
"n": 0,
"tx_index": 6788412058082531,
"script": "a914e1784750b953ffd9d72ba65035e33eac53758ea387",
"addr": "3NFC3onoBpTSvBs5XU3zb9Z5kwSnfA8gEc"
},
{
"type": 0,
"spent": false,
"value": 1673050,
"spending_outpoints": [],
"n": 1,
"tx_index": 6788412058082531,
"script": "76a914224643d8742fa4c2545e69fa54a945dff1ff084688ac",
"addr": "148E9d3oRzZERz8D7gryh1MV2XQVvr2Tpv"
}
]
}
Without pretending to cover in detail how transactions work, which will be done in a separate lesson, we can say that transactions in Bitcoin contain one or more inputs (which can be seen as debits to an account) and one or more outputs (which can be seen as credits to an account).
For one user to be able to send bitcoins to another, all he needs to know is their bitcoin address.
Obviously, the sum of the inputs must be greater than or equal to the sum of the outputs, or else it would be like paying for the 15 euros at the supermarket with a 10 bill.
Each transaction requires payment of a fee, called a transaction fee, which can be quantified as the difference between the inputs and the outputs. Why this fee must be paid will be explained in the next chapter on mining.
Another fundamental concept to understand is that the inputs of a transaction are nothing more than the outputs of previous transactions.
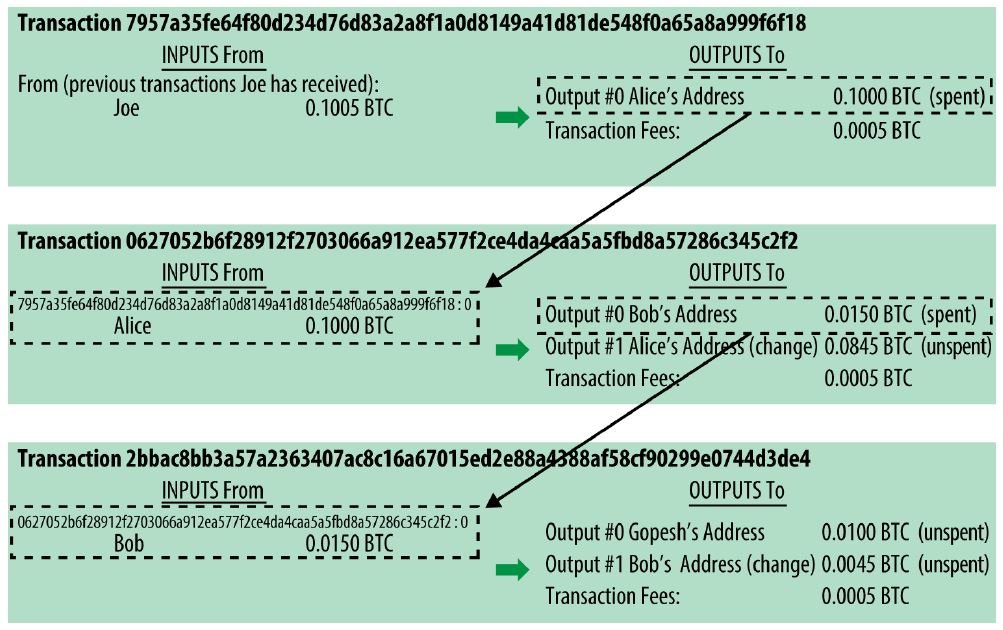
In this way, the transactions are connected to each other, allowing the origin of the bitcoins to be easily traced, and thus allowing the validity of a transaction to be indisputably verified (e.g., I can send 10 bitcoins because I received them in precendence), thus avoiding problems such as double-spending.
Transaction outputs can be seen as the building blocks of bitcoin, specifically the unspent outputs, called UTXO (Unspent Transaction Outputs).
In the image we can see the chain of transactions, going all the way down to the last one whose outputs are UTXOs because they have not yet been spent.
We can go further and then say that the balance of a given account is the sum of all the UTXOs of the transactions to it.
Let us return to Alice and Bob.
Assume that Alice has to send 1 BTC to Bob and that she has 3.1 BTC, which is the sum of all the UTXOs destined for her.
Specifically, suppose there are fees per transaction of 0.1 BTC and that Alice received the 3.1 BTC from 3 transactions: one from 2 BTC, one from 0.6 BTC, and one from 0.5BTC.
It is critical to understand that Alice will not be able to break the 2 BTC UTXO, using only 1 BTC.
The cash metaphor comes in handy; Alice will be able to pay the 1 BTC to Bob in two ways:
- By adding up the two 0.6BTC and 0.5BTC UTXOs;
- By using the 2 BTC UTXO, from which she must somehow receive change.
In the first case, the sum of the inputs will be 1.1 BTC. The output will be only one, 1 BTC intended for Bob. The fees will be 1.1 – 1 = 0.1 BTC.
The second case is more complex because, exactly as in the supermarket example, Alice will have to receive change. In fact, if the transaction had only one input of 2 BTC and only one output of 1 BTC, intended for Bob, Alice would pay 2 – 1 = 1 BTC in commissions without receiving any change.
To avoid this, Alice will have to enter a second output, containing a so-called change address, i.e., a new address belonging to Alice to be used to receive change.
In fact, Alice cannot enter among the outputs the address from which she is sending the BTC, but must create a new one, the change address precisely, to which to send the change.
The transaction will thus have two outputs: 1 BTC destined for Bob and 0.9 BTC destined for the new change address.
Again, it is simple to calculate the fees, which will be 2 – 1 – 0.9 = 0.1 BTC.
At this point Alice will have to provide proof that she actually created the transaction and will do so by creating a digital signature through her private key.
It should be specified that all the steps seen so far take place offline.
Once the transaction is completed, it must be transmitted to the Bitcoin network. To do this, it must go through a node (it does not matter the type of node, as long as it is connected to the Bitcoin network).
The node will check if it is a new and valid transaction and if so, it will propagate it to the other nodes it is connected with, which will do the same thing in turn.
To get a visual representation of this propagation mechanism, we refer to this page(https://ctufaro.github.io/GossipPlot/index.html), where we can observe the progressive propagation of a message within the Bitcoin network.
In this way, the transaction will become part of the mempool, which is the space in which all valid transactions that have not yet been placed within a block on the blockchain stand.
At this point we move on to the block creation phase, which we will see in the next chapter.
The one presented is the simplest example of a transaction, but in reality there are far more complex ones, with many inputs, many outputs (perhaps destined for different addresses) or even transactions with inputs coming from different addresses.
In addition, it should be emphasized that the concepts presented here are barely sufficient to explain how high-level transactions take place, for example by making a transaction from a mobile wallet.
In reality, beneath the surface, the mechanism is much more complex and will be explored in more detail in the dedicated lectures.
Mining and consensus
We have reached the point where Alice’s transaction to Bob has been propagated through the network and has entered the mempool, so it is waiting to be inserted within a new block.
The process called mining and Bitcoin’s consensus protocol, Proof of Work (PoW), come into play at this point.
Often mining is seen exclusively as a way to obtain rewards, in reality it is this process that the entire operation of the Bitcoin blockchain is based on.
It is in fact through mining that transactions are placed within new blocks, which are then added to the blockchain, thus making them confirmed.
The problem that arises at this stage is that of distributed consensus. That is, in a decentralized network, such as the one described so far, how does each node in the system arrive at the same version of the ledger that can be trusted?
In a centralized network, the central entity is in charge of determining what is true and what is false, and all other actors place trust in this entity.
In a system like Bitcoin, which is called trustless, nodes reach consensus without the need for this central entity.
All the more so since the network is asynchronous, so not all nodes get information at the same time.
This problem is solved through the emergent consensus mechanism proposed by Satoshi Nakamoto.
Through this process, consensus emerges implicitly, without the need for elections, through four independent processes:
- Verification of eachtransaction, by each full node;
- Aggregation of the valid transactions into new blocks by the mining nodes, who must also provide evidence to prove their work;
- Verification of new blocks by each node in the network;
- Selection of the chain with the greatest computational power
Back to Alice’s transaction, after sending it to a first node, it will verify the validity of the transaction by checking a number of conditions within the Bitcoin code (e.g., correct syntax, non-empty input and output, etc.).
Only if the transaction is found to be valid will the first node propagate it to the nodes it is in communication with, which will perform the same checks and, if valid, propagate it in turn.
So we have here a first layer of security, a selection of valid transactions to be propagated by all full nodes, those that own a copy of the register.
As we had already mentioned, the valid transactions will go into the mempool of each node that received the transactions, waiting to be inserted into a new block.
This brings us to the second process, which this time involves a different type of nodes: miners.

The miners compete with each other for the creation of the new blocks. What they do is take transactions from the mempool, group them together and create a header for the new block, which will contain data about the block. At this point they will have a candidate block, but to be proposed to the network, it must also possess proof of work done by the miner (hence Proof of Work).
The proof of work required of the miners consists of solving a very complex cryptographic puzzle, which requires a great deal of computational power to solve and therefore a large amount of power consumption.
Each block is identified by a 256-bit string that is obtained through a hash function known as SHA256.
We have already mentioned hash functions in the course of this overview; they are functions that take as input a string of variable length and return as output a string of fixed length (256 bits in the case of SHA256), with the peculiarity that, while computing the output from the input is a computationally uncomplicated operation, the reverse operation is practically impossible.
Moreover, a slightest change in the input, leads to a completely different output.
These are functions that underlie Bitcoin’s cryptography, starting with key generation, which we have already addressed.
Miners have to find the hash of the new block they will propose to the network, and to do this they have to pass as input to SHA256 the candidate block.
The hash then will depend on the content of the block, both the information in the header and the transactions.
| Field size | Description | Data Type | Comments |
|---|---|---|---|
| 4 | version | int32_t | Block version |
| 32 | prev_block | char | Hash of the previous block |
| 32 | merkle_root | char | Reference to a Merkle tree that is a hash of all transactions related to this block |
| 4 | timestamp | uint32_t | Timestamp of when the block was created |
| 4 | bits | uint32_t | The difficulty of the target used for the block |
| 4 | nonce | uint32_t | The nonce used to generate the block |
| 1 | txp_count | var_int | Number of transactions |
We are particularly interested in the header because, among other information, it contains three that we are interested in at this stage:
- Thehash of the previous block;
- The target of the Proof of Work algorithm for the candidate block;
- The Nonce.
The hash of theprevious block makes the hash of the candidate block, which the miner is working on, dependent on the previous block, which in turn is dependent on the one before it, and so on.
This creates an inseparable blockchain, from which the name blockchain is derived, in which each block is related to the previous block.
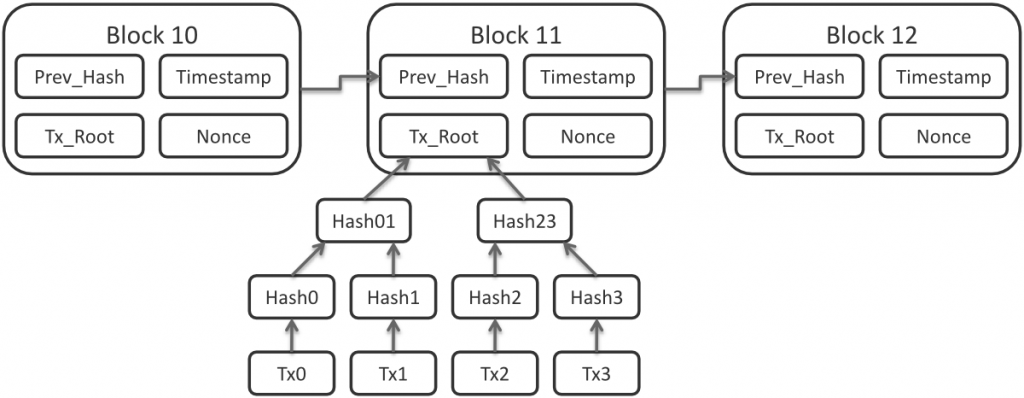
The target and nonce, on the other hand, concern the work to be done by the miner.
The target defines precisely a certain goal that the miner must achieve: the hash of the new block must be less than the target.
The nonce, on the other hand, is a variable number that is used to make the output of a hash function change.
We mentioned that changing even one character of the input leads to a different output. By changing the nonce, the miners try to find a hash that is less than the established target.
The only way they can do this, since it is impossible to trace the input from the output, is through bruteforce, that is, trying with nounce, until they randomly find the one that gives the result below the desired target.
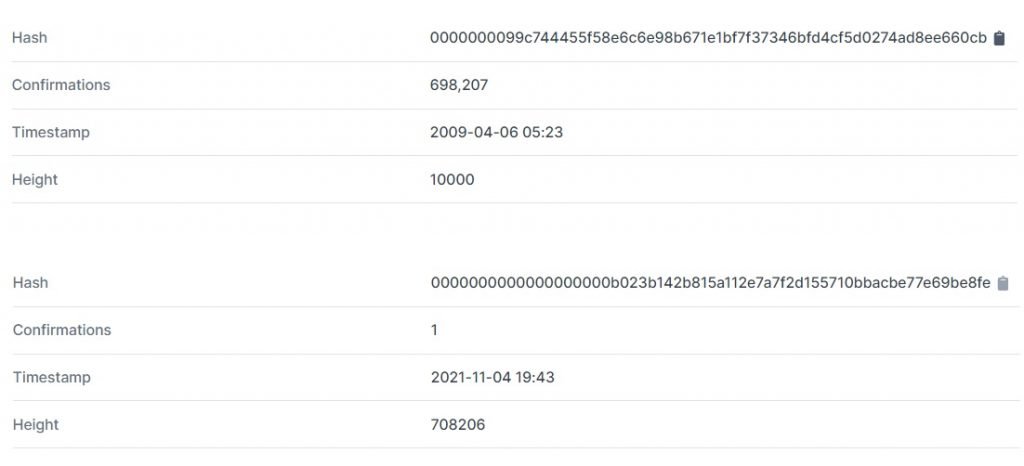
If you look at the hash of a very old block and that of a recent block, you can see that the number of zeros at the beginning of the hash has increased significantly. This means that the target required by the recent block was smaller.
It is necessary to introduce a concept that may be counterintuitive: the smaller the target, the greater the computational difficulty. From this we can infer that the difficulty of the blocks has increased over time, as we will explain shortly.
Surely you are wondering: why would miners want to use so much computational power, spending money on electricity, to create new blocks?
Satoshi Nakamoto has provided two rewards to incentivize miners to play this role:
- Transaction fees;
- New bitcoins that are created from scratch (mined precisely) with each new block.
The former, seen above, are obtained by subtracting the sum of all the block’s transaction inputs from the sum of all the block’s transaction outputs.
Regarding the second point, the miner inserts into the candidate block, in addition to the transactions selected by the mempool, a special transaction, which will always be the first in the block, called coinbase.
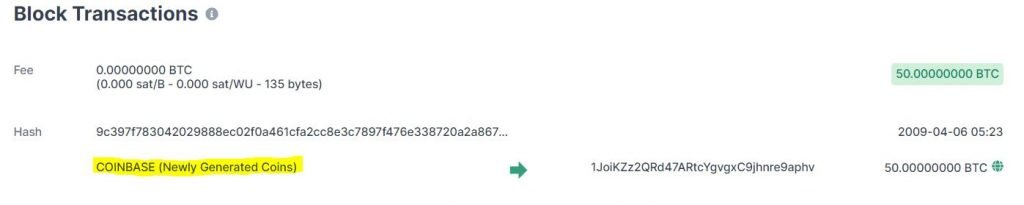
In this transaction, new bitcoins, created from scratch, are mined and sent to the address entered by the miner.
The bitcoins mined at each bocco halve every 4 years or so, to be precise every 210000 blocks, according to the process called halving seen earlier, which is used to distribute bitcoins more and more slowly, until max sypply is reached, as explained in the dedicated chapter.
When we say about 4 years, it is because a new block is created on average every 10 minutes.
As one can easily guess, finding the correct nonce becomes easier as the computational power of the Bitcoin network increases, which is why every 2016 blocks, the target is updated taking into account the total computational power of the network. If the computational power is increased, the target will decrease, making it more difficult to solve the cryptographic puzzle. Conversely, as the computational power of the network decreases, the target will increase, making it easier to find a correct nonce.

Let us return again to the Alice transaction: after being propagated in the network, we assume that miners will have placed that transaction in their candidate block.
In the best case, only one miner will arrive at the solution to the cryptographic puzzle and, as soon as it is reached, will propagate for the network its block containing the proof of its work.
At this point the third process begins, the verification of the blocks by the network.
The nodes, once they receive the block, validate it, performing various checks provided by the Bitcoin code (correct data structure and syntax, minor hash of the target, etc.).
If the block is found to be valid, they will add it to their local ledger and propagate it to the nodes they are in communication with.
At this point, this new version of the registry will begin to propagate, and when it reaches the miners that were working on the new block, they will realize that they have lost the competition for that round and will immediately get to work on the next block.
It is worth emphasizing one point from what has been said so far, concerning how consensus is expressed in the bitcoin network.
As mentioned above, consensus emerges implicitly, without the need for elections or anything else.
We need to distinguish between miners and other nodes.
In both cases, voting is expressed by adding a new block to their register or not. In the case of miners, however, there is a subtlety to consider: miners implicitly cast their vote when they start creating a new block by entering the hash of the previous block.
This is particularly relevant in cases where, unlike in Alice’s example, two miners (C and D) reach the solution of a block within a short time interval.
The two miners will propagate their blocks, both of which are valid, and the network will split into two parts. Some nodes will have received one block first while others will have received the other first.
In these cases, a phenomenon called blockchain fork occurs. The distributed ledger will be split into these two versions, both of which are valid, and this bifurcation of the chain will continue until one of the two branches has greater cumulative computational power, which, in most cases, happens directly at the next block.
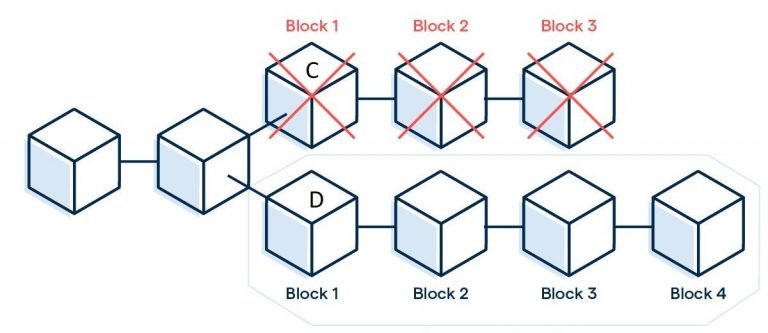
In fact, the miners will immediately start building the new block. Some of the miners will build it from the block of C and some will build it from the block of D.
The first miner with a valid block will propagate it to the network, implicitly casting its vote for the previous block (in this case D) and leading the network to revert to distributed consensus.
The block that does not prevail will be deleted and the transactions within it will return to the mempool.
In this way, each block will receive a number of confirmations equal to the number of blocks following it. The more confirmations there are, the more transactions within it are to be considered immutable, and usually 6 confirmations are considered to be absolutely certain that a transaction has entered the register.
Process Overview
The whole process described is simpler than you might think, and by way of summary we now give an outline of the 9 main steps:
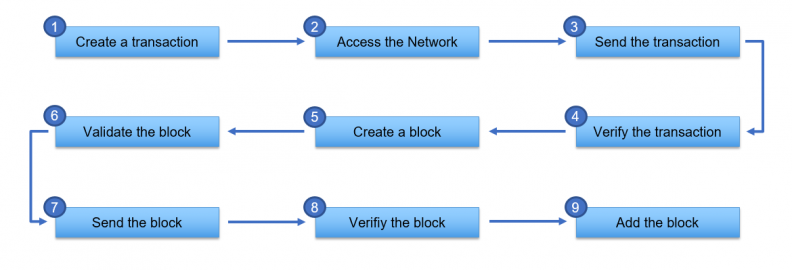
- Creating a transaction: a person who wants to send bitcoins to another person creates an offline transaction with the structure seen above. This does not mean that bitcoins are already transferred, it just means that the transaction text has been written.
- Network access: Once the transaction is completed, it must be transmitted to the bitcoin network. For this to happen, it must pass through a node (it does not matter the type of node, as long as it is connected to the Bitcoin network).
- Sending the transaction: the transaction is sent to all nodes in the network, so that everyone can see that this person wants to send those bitcoins to another person. Everyone has visibility of the sender and receiver addresses, but no one knows who (first and last name) is in fact the person behind those addresses.
- Transaction verification: after all nodes in the network receive the transaction, they perform some checks, including:
- they check if the structure of the transaction is correct;
- they check whether the input of the transaction is linked to the outputs of previous transactions, that is, they check whether the sender of the transaction really has the bitcoins it is sending by looking at the history of transactions linked to the sender’s address in the register.
- Create a block: all verified transactions go into the mempool, the waiting room for unconfirmed transactions that have not yet been included in a block. There, all validator nodes, the miners, select a group of transactions by looking at the maximum block space available and the fee for each transaction, and each starts creating a new block containing the selected transactions. Thus, different miners can create different blocks by entering different transactions.
- Block validation: all miners begin to participate in a mathematical game, called Proof of Work (PoW), which, as the name suggests, is intended to prove that work is being done to solve the game. Simply put, this mathematical game is performed automatically by the computer and depends both on the computer’s available computational capacity and partly on the luck of the miner who is trying to validate his or her created block. The proof of work consists of finding a nonce, a variable number that is difficult (expensive and time-consuming) to produce but easy to verify by others. If a miner finds the block nonce, he wins the PoW and his block is validated.
- Sending the block: the miner who wins the PoW transfers the validated block to all other nodes in the network. In return for his work, the miner receives an amount of bitcoin that is minted for each new block created (the amount changes every 4 years due to the halving process) and the fees associated with each individual transaction entered into the validated block.
- Block verification: each node in the network receives the validated block and verifies that it contains only valid and correct transactions. It may happen that two miners find the solution for their block at the same time (blockchain fork phenomenon): in these cases, the nodes receiving the new blocks start working on the first one they receive and eventually the longer chain is maintained.
- Block addition: if in the verification phase the consensus expressed by the nodes is positive, each node adds the newly verified block to its blockchain register.
The register then results in a succession of blocks concatenated with each other and contains the entire ordered sequence of blocks with their respective transactions inside.
Governance and protocol changes
Another very important aspect to consider is that of Bitcoin’s governance.
We have seen that Bitcoin is decentralized and that the consensus protocol provides a set of rules. These, however, although immutable in the short term, can change in the long term.
There have in fact been updates to the protocol and will continue to be, although they are difficult because they require coordination among the various actors that are part of the Bitcoin ecosystem.
Indeed, we can identify several groups of actors within the ecosystem:
- Miners;
- The core developers;
- The full nodes;
- The end users;
- The financial actors (such as the exchanges).
These groups often have conflicting interests, and any changes to the consensus protocol must mediate between the needs of all to be approved.
An interesting example is that of the block size war, or the debate that has developed over a number of years about increasing block size.
We will cover the block size war in a dedicated lecture, because it was a very important event for Bitcoin, which makes it very clear how power is distributed among the various parties.
Without going too much into specifics, here we will just make the distinction between the two ways in which changes can be made to Bitcoin’s protocol:
- Hard Forks;
- The Soft Forks.
We have already encountered the word fork when we talked about Blockchain Forks. In that case, following a momentary split of the chain into two branches, we reverted back to the unique consensus, choosing one of the two branches.
Different is the case with hard forks, which are changes to consensus rules that cause the Bitcoin network to split into two parts: nodes that accept the new rules and nodes that do not.
The chain thus branches off and the two branches continue on their own paths, independent of each other.
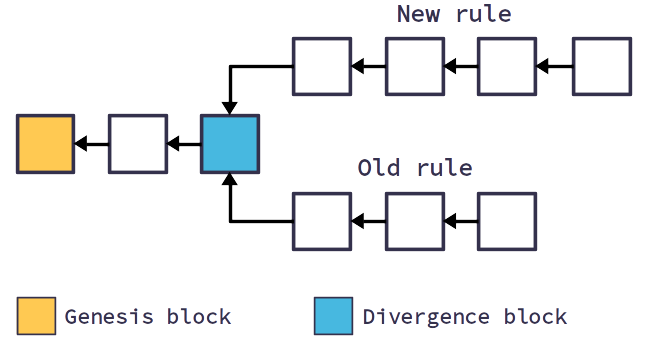
Of course, for a hard fork to occur, there must first be a change to the Bitcoin client, brought about by developers.
Then this client must be chosen by some of the nodes in the network, and in this way the network will split into the two factions.
It is understood that this is a drastic solution, which is very complicated because it leads to the network splitting and no longer being able to cooperate.
In contrast, soft forks are changes to the consensus rules, without the need for the network to split, leading the blockchain to bifurcate.
Soft forks are only possible when the rule changes are forward-compatible, that is, in cases where a client that does not have the new consensus rule changes can still continue to participate in the protocol with the previously valid rules.
As can be inferred, the expression soft fork is misleading because, in fact, there is no fork.
It should be noted that in order to have a soft fork, rule changes can only restrict existing rules, not expand them, in order to be backward compatible.
A map of Bitcoin forks can be seen in the following image.

Balancing the needs of the various parties is one of the reasons Bitcoin is truly decentralized.
Think, for example, of an update to the consensus rules proposed by developers. They have the power to change the code, but it is not certain that the network nodes will then decide to adopt the updated client.
One of the issues that is often raised is that of mining pools, which are groups of miners who aggregate their computational power in order to have a better chance of solving cryptographic puzzles and thus being rewarded for their work.
One of the theoretical scenarios that could jeopardize the health of the Bitcoin network is a 51 percent attack, which is the case if a single pool were to have more than 50 percent of the overall computational power of the Bitcoin network, and were to use it for malicious purposes.
Beyond the fact that, achieving such computational power, in practice, is extremely complex, if not impossible, in any case, the miners remain only one of the groups that make up the Bitcoin ecosystem.
The other groups may decide to stop following the malicious pool and keep the economy in an honest part of the chain. Malicious miners would then find themselves mining empty blocks.
Layer 2 – Lightning network
Despite all the positive aspects that should emerge from this overview, there remain critical aspects of Bitcoin that are often challenged against it.
We often hear that Bitcoin has high transaction fees. Or that it cannot scale because blocks are created every 10 minutes and average transactions per second are about 7, a number infinitely lower than circuits such as Visa, but also compared to other cryptocurrencies.
These wait times make Bitcoin impractical for microtransactions.
Or again, they challenge the limited nature of Bitcoin which lacks, for example, the smart contracts of Ethereum and many other projects, even though, in reality, Bitcoin has a scripting language that underlies every transaction and is used to create some sort of smart contracts, but that is too in-depth a topic for this overview.
Developers try to solve some of these limitations by updating and modifying Bitcoin’s rules, as seen in the previous chapter, but there are other possible solutions.
One of these is layer two applications.

In blockchain, one of the main problems is the famous blockchain trilemma, according to which it is impossible for a blockchain to be decentralized, scalable and secure at the same time.
Many have tried to solve the trilemma directly layer one, that is, at the consensus protocol level, such as Silvio Micali with Algorand.
Many others, however, argue that it is impossible to solve the trilemma by remaining layer one and that the only way to do so, is by using layer two applications, that is, solutions that operate outside the blockchain and the core network.

There are many such solutions to extend the potential of Bitcoin, one of which is the Lightning Netowrk.
This is an off-chain solution that allows for micro-transactions with very low fees and great speed, without clogging up the main chain, with which the Lightning Network communicates as little as possible, only when strictly necessary.
In short, it is a network built on the Bitcoin network, which we will elaborate on in a dedicated lesson.


